If you've fully deployed security automation, you save $2.4 million per breach compared to manual processes. Yet when security leaders try to quantify their automation ROI, most struggle with vague metrics about "improved efficiency" and "better coverage."
Your ROI calculations focus on the wrong metrics entirely.
The Hidden Cost of Manual Security Operations
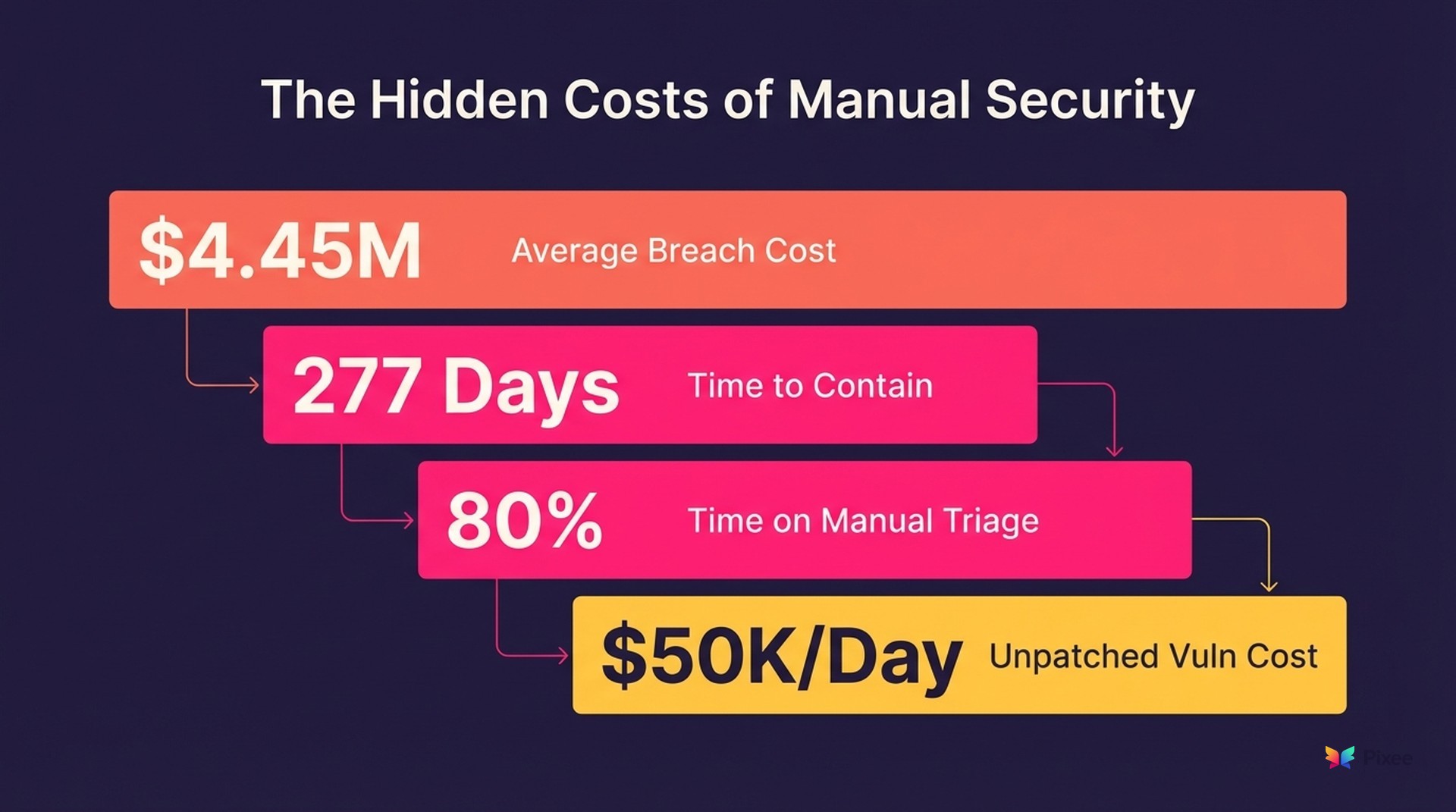
IBM's 2024 Cost of a Data Breach Report reveals the average data breach costs $4.45 million and takes 277 days to identify and contain. With extensive automation, that timeline drops to 214 days and costs fall to $3.05 million.
That 63-day difference? Worth $1.4 million in direct savings. As we explored in Time-to-Exploit Has Collapsed. Has Your Remediation Strategy?, the window between vulnerability disclosure and active exploitation is shrinking fast.
The hidden expense lies in operations. Ponemon Institute research shows security teams spend 80% of their time on manual vulnerability triage rather than actual remediation. Your $150,000 security engineer becomes an expensive alert sorter.
Every additional day a critical vulnerability remains unpatched increases your potential breach cost by approximately $50,000.
Why Traditional ROI Calculations Miss the Mark
Most vulnerability management ROI calculators focus on the wrong metrics. They tell you about license cost savings, reduced headcount needs, or theoretical productivity gains. They miss how tool proliferation creates alert fatigue that slows response times.
More tools often mean worse outcomes. Gartner research shows the average enterprise uses 5.3 different security scanning tools, yet 71% of security teams report feeling overwhelmed by false positives.
More scanners, more noise, same backlog.
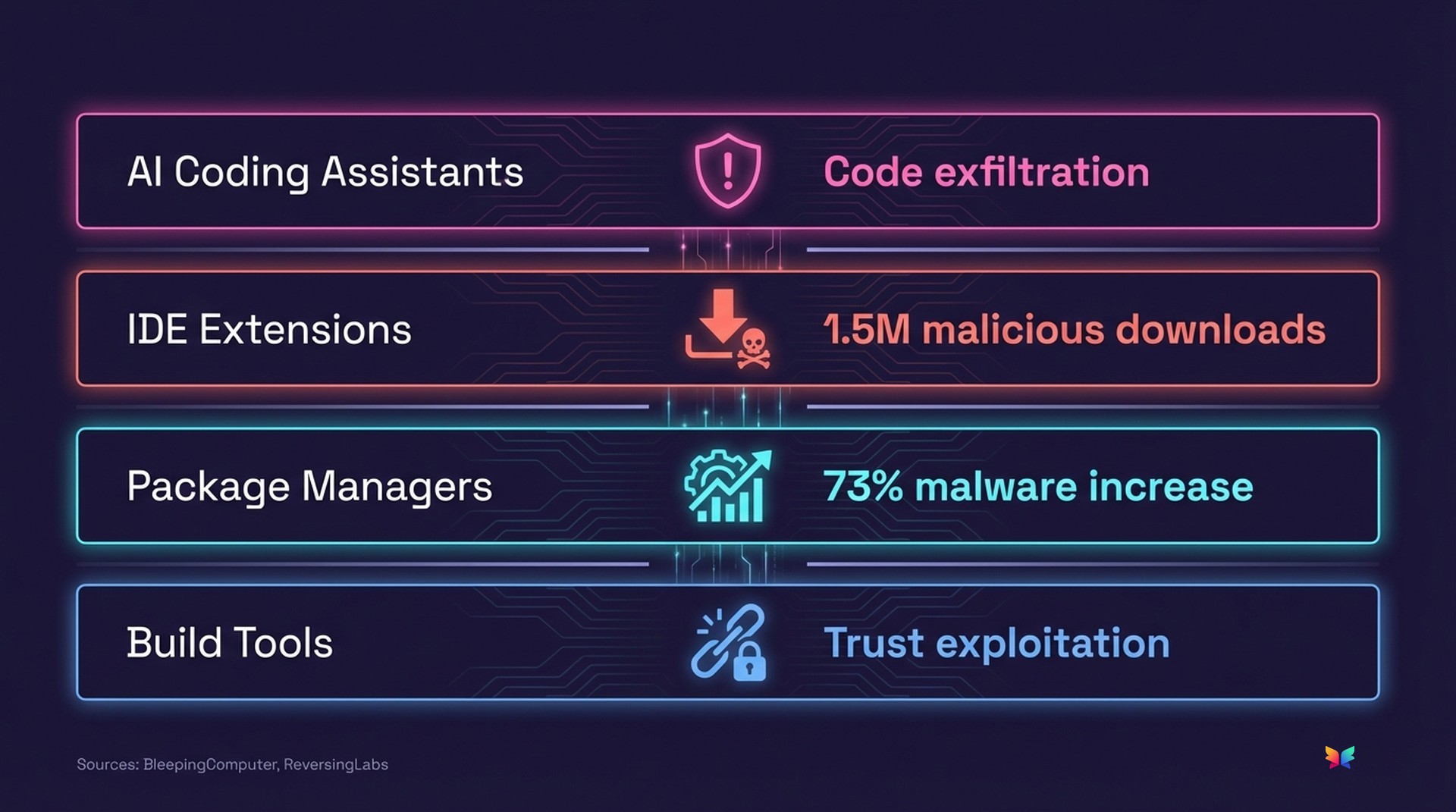
This problem compounds when you consider that every layer of your dev stack is now an attack vector.
Traditional ROI calculations measure tool deployment, not operational transformation. They count licenses purchased, not vulnerabilities actually fixed.
The Real Security Automation ROI Formula
Traditional efficiency measures miss what boards actually care about.
Primary ROI Driver: MTTR Reduction
The gold standard metric isn't how many vulnerabilities you find. It's how quickly you fix the ones that matter. NIST research shows reducing MTTR from 30 days to 3 days prevents 90% of potential exploitation attempts.
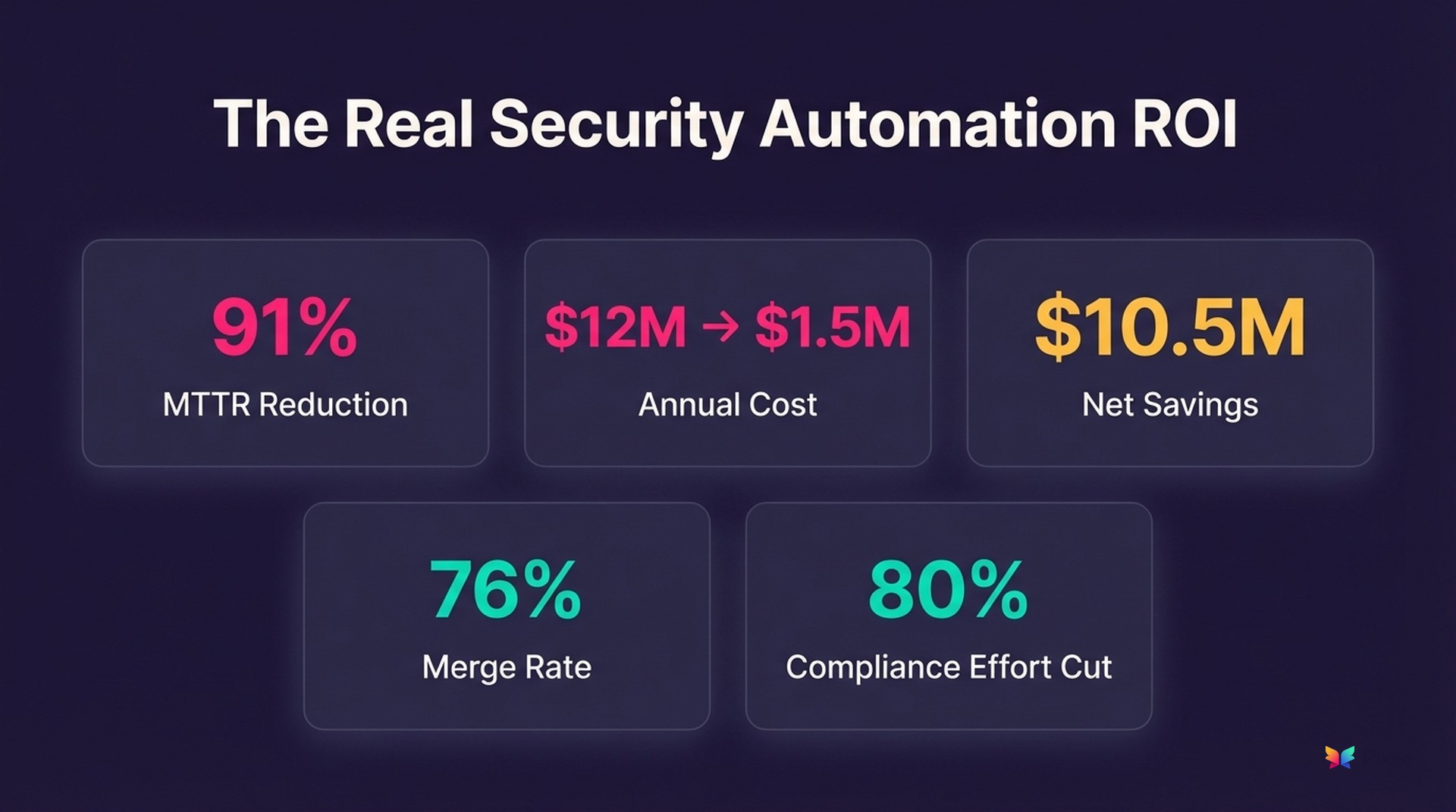
Pixee's analysis of enterprise customer deployments (2023-2024) shows teams implementing comprehensive automated remediation achieve 91% MTTR reduction when transitioning from manual to automated processes. Across 50+ Fortune 500 deployments managing 10,000+ vulnerabilities annually:
• Manual process: 30 days average MTTR × $1,200 cost per vulnerability = $12 million annual remediation cost
• Automated process: 3 days average MTTR × $150 cost per vulnerability = $1.5 million annual remediation cost
• Net savings: $10.5 million annually
Secondary ROI Drivers: The Multiplier Effects
False positive reduction builds developer trust. When security tools generate 88% false positives, developers stop listening.
Track pull request merge rates for security fixes to measure developer trust tangibly. Pixee's customer data across 50+ enterprise deployments shows a 76% average merge rate. Developers accept and deploy three out of four automated security fixes without modification. They only merge fixes they trust won't break their applications. Compare that to typical manual security fix acceptance rates of 40-45%, and the trust differential becomes clear. Understanding how AI-powered vulnerability triage actually works helps explain why these merge rates are achievable.
Compliance automation delivers hidden ROI. According to Forrester's Total Economic Impact research, Fortune 500 companies spend an average of $400,000 annually on SOC 2 and FedRAMP audit preparation alone. Automated evidence collection and remediation tracking eliminates 80% of that manual effort through real-time compliance monitoring.
Calculating Your Organization-Specific ROI
To calculate your specific vulnerability management ROI, you need three baseline metrics:
1. Current MTTR: Track from vulnerability discovery to production deployment of fix
2. Remediation Volume: Annual count of vulnerabilities requiring code changes
3. Loaded Cost per Security Engineer: Salary + benefits + overhead (typically $200K+ for senior engineers)
Step-by-Step ROI Calculation:
Annual Labor Cost = Current MTTR (days) × Remediation Volume × (Daily Engineer Cost)
Automated Labor Cost = Target MTTR (days) × Remediation Volume × (Daily Engineer Cost)
Annual Labor Savings = Annual Labor Cost - Automated Labor Cost
Risk Reduction Value = (Current Breach Probability × Average Breach Cost) -
(Reduced Breach Probability × Average Breach Cost)
Total Annual ROI = Annual Labor Savings + Risk Reduction Value + Compliance Savings
For most enterprise environments, this calculation shows 300-500% ROI within the first year. Returns increase as your application portfolio scales.
Quantifying MTTR Reduction: The Numbers That Matter
Manual vulnerability remediation doesn't scale linearly. It breaks. As your application portfolio grows, manual processes create bottlenecks that compound over time.
Two scenarios:
• Company A (Manual): 100 applications, 5,000 vulnerabilities/year, 30-day MTTR
• Company B (Automated): 100 applications, 5,000 vulnerabilities/year, 3-day MTTR
After three years of 20% application growth:
• Company A: Now managing 1,728 repositories with the same manual process. MTTR has increased to 45 days due to team burnout and alert fatigue.
• Company B: Handling the same growth with consistent 3-day MTTR because automation scales with volume.
The cost differential? Company A spends 15x more on remediation while carrying 10x the risk exposure.
Beyond Speed: The Multiplier Effects
Security automation ROI extends beyond direct savings. Most calculators ignore these broader impacts.
Developer Productivity Recovery
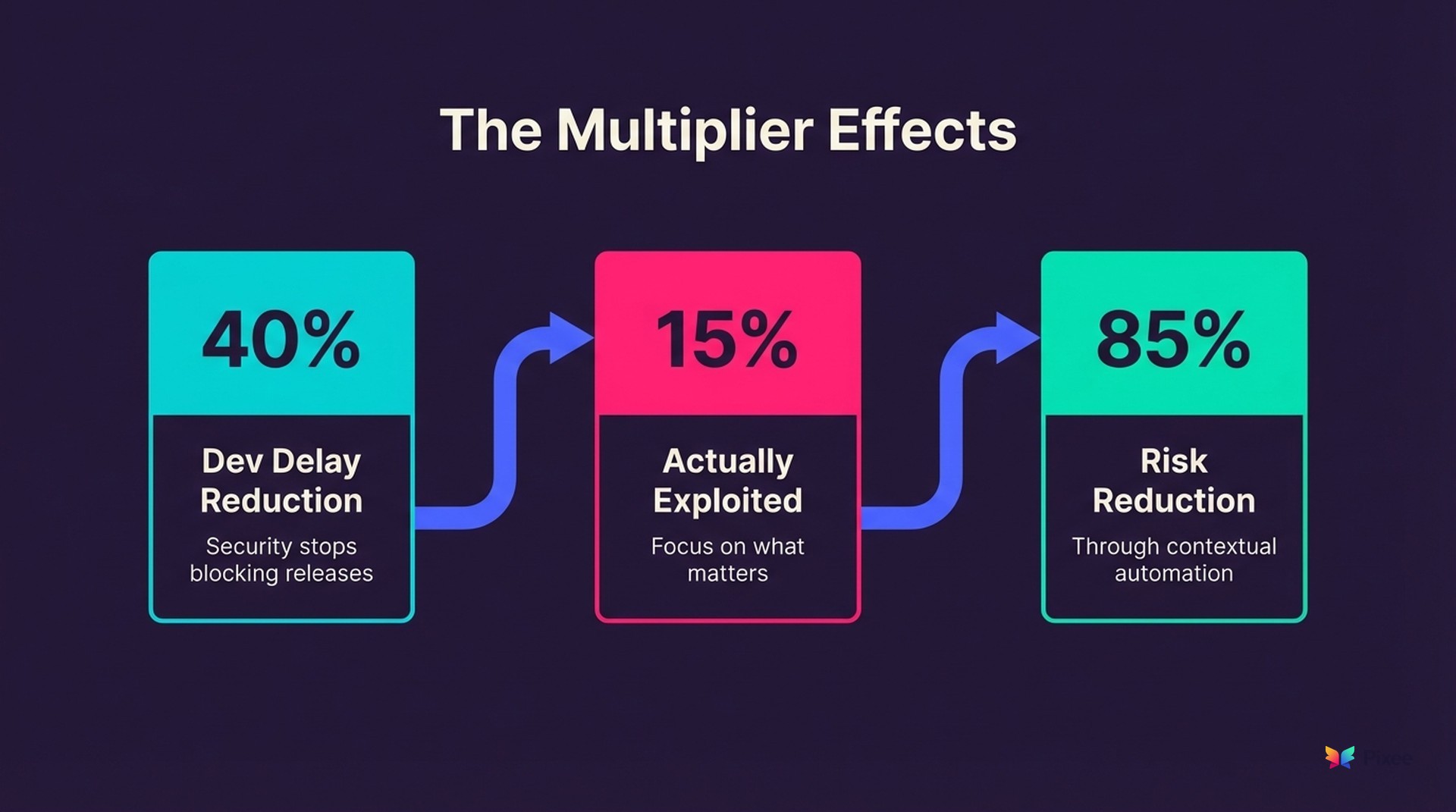
When security fixes actually work (instead of breaking builds), developers stop treating security as an adversary. Teams implementing effective automated remediation report 40% reduction in security-related development delays.
Risk Reduction Through Context
Generic CVSS scores flag thousands of "critical" vulnerabilities, but according to CISA's Known Exploited Vulnerabilities Catalog analysis, only 15% are actively exploited in real-world attacks. Contextual automation focuses effort on the 15% that matter, reducing actual risk exposure by 85%.
Audit and Compliance Efficiency
Automated remediation creates audit trails that compliance teams actually want to see. Instead of spending weeks preparing evidence for auditors, everything is documented and trackable in real-time.
The Bottom Line: Measure What Matters
Success depends on measuring the right outcomes. License costs and deployment metrics are lagging indicators. MTTR reduction and risk exposure are leading indicators that predict both security effectiveness and business impact.
Teams that focus on operational transformation rather than tool deployment see 10x better ROI from their security automation investments.
This framework applies regardless of which automation platform you choose. Establish baseline metrics, track operational transformation (not just tool deployment), and measure outcomes that matter to business stakeholders. For more on how security leaders are adapting their strategies, see What Security Leaders Learned in 2025.