The tools you trust to build software are being turned against you.
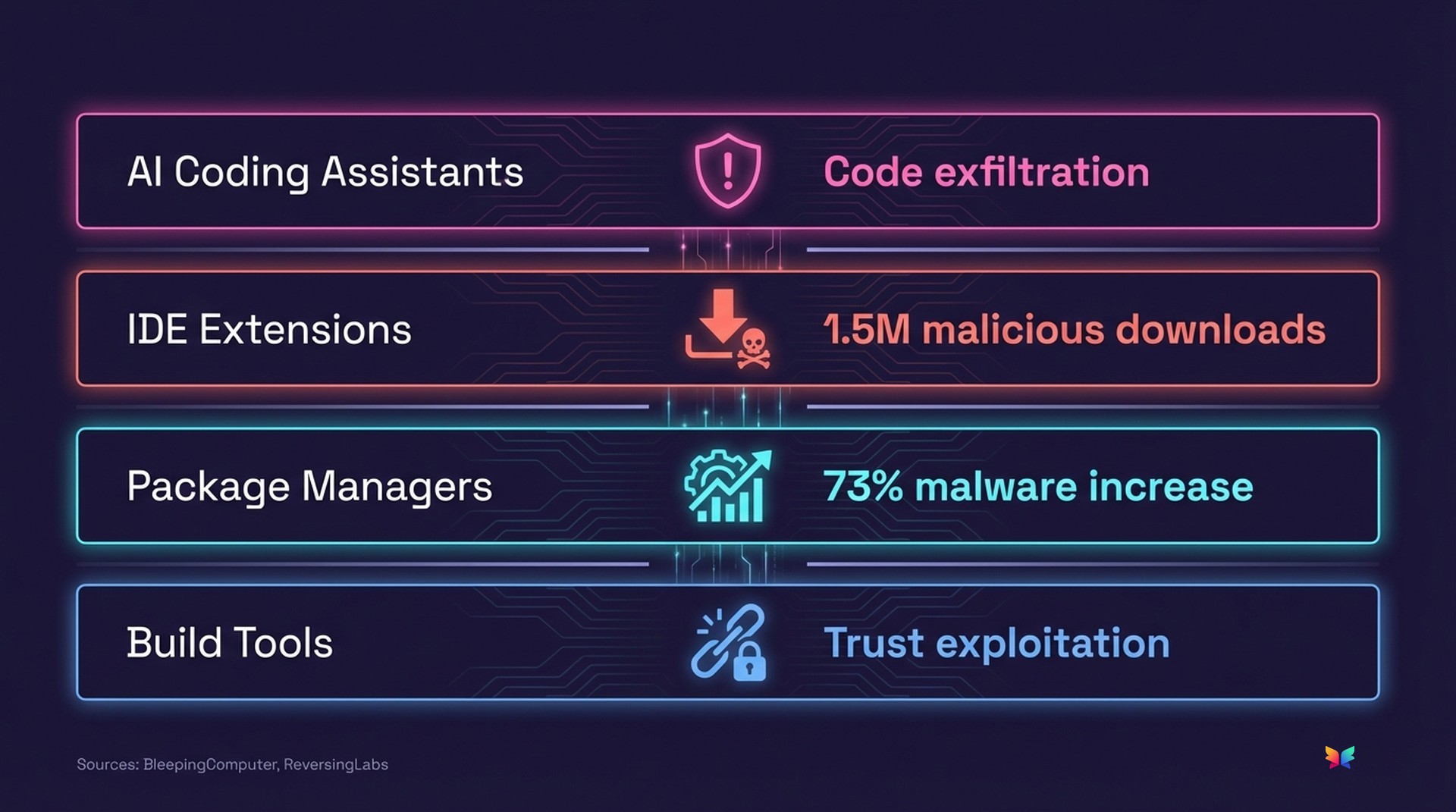
Three converging threats should change how you think about developer toolchain security: malicious VSCode extensions with 1.5 million downloads, a 73% surge in npm malware, and AI coding assistants that provide real functionality while silently exfiltrating your code.
What is developer toolchain security? The practice of securing the entire software development environment—IDE extensions, package managers, build tools, and AI coding assistants—with the same rigor applied to production infrastructure, including access controls, dependency auditing, and network monitoring.
Package managers. IDEs. AI assistants. Each represents a trust relationship that attackers now systematically exploit. Here's what's happening at every layer and what defense actually looks like.
The IDE Extension Attack Surface
Two VSCode extensions accumulated 1.5 million combined downloads before anyone noticed they were stealing developer data.
The breakdown:
ChatGPT Chinese version (1.34 million installs) and ChatMoss (152,000 installs). Both extensions passed Microsoft's marketplace review process. Both provided fully functional AI assistant capabilities. Both silently exfiltrated code to China-based servers. Aikido Security separately documented the Fake ClawdBot extension using similar tactics.
The extensions remained on the marketplace for three days after security researchers disclosed the threat. Three days where developers continued downloading and installing malware that had already been publicly identified.
The attack pattern is particularly insidious because the extensions delivered real value. Developers weren't installing empty shells or obvious fakes. They were installing functional AI assistants that worked as advertised while maintaining a secondary exfiltration channel.
Developer machines aren't just workstations. They hold source code, deployment credentials, API keys, and often direct access to production systems. A compromised development environment isn't a minor incident. It's a pathway to everything your organization builds and operates.
Package Managers Under Siege
The numbers from ReversingLabs' 2026 report are stark: malicious open-source packages increased 73% in 2025, with malicious activity on npm more than doubling. Of all malware detections across package ecosystems, npm accounts for 90%.
The G_Wagon malware campaign demonstrates the evolving sophistication. Distributed through npm packages, G_Wagon targets over 100 cryptocurrency wallets along with browser credentials and session tokens. It harvests everything valuable on a developer's machine.
The platform response to supply chain threats has created a two-tier security ecosystem. When researchers at Koi Security disclosed six zero-day vulnerabilities across JavaScript package managers, the responses diverged sharply:
• pnpm shipped fixes in 2 weeks
• vlt patched in 8 days
• Bun resolved issues in 3 weeks
• npm closed the report as "works as expected"
npm's official position: "npm users are responsible for vetting the content of packages that they choose to install." That leaves development teams vulnerable to supply chain attacks and requires them to implement their own rigorous package vetting processes. Organizations using pnpm or Yarn get platform-level protections. Organizations using pnpm or Yarn get platform-level protections. Organizations locked into npm inherit continuous vetting responsibility themselves.
As pnpm documented in their enterprise case study, security-conscious organizations are explicitly migrating away from npm for this reason.
Package manager selection is now a security decision, not just a features comparison.
The Trust Model Is Broken
Every layer of the modern development stack represents a trust relationship:
• You trust the package manager to prevent malicious packages
• You trust the IDE marketplace to review extensions
• You trust AI assistants to process code without exfiltrating it
• You trust build tools to execute only what you intend
Attackers are probing each of these relationships systematically.
Traditional dependency scanners miss IDE extension threats entirely. They're designed to analyze package manifests and dependency trees, not evaluate what browser extensions or IDE plugins are doing with your data. As the research notes: "Popular" ≠ "Safe."
Download counts create a false sense of security. The malicious VSCode extensions had millions of downloads. High download numbers signal popularity, not safety. Attackers understand this and target high-visibility distribution channels specifically because volume provides cover.
The detection gap is systemic. Microsoft's marketplace review process approved these extensions. They accumulated massive download counts over time. The extensions were functional—they delivered real AI assistant capabilities. Detection came from external security researchers, not platform controls. Even after public disclosure, the extensions remained downloadable for three additional days.
The core problem goes deeper than any single vulnerability. The tools you use daily operate in a trust model designed before these attack patterns existed.
Developer Toolchain Security: Defense in Depth
Treating your toolchain with the same rigor as production infrastructure means implementing controls at multiple layers.
Extension hygiene: Maintain an allowlist of approved extensions for your organization. Require justification for additions. Evaluate extensions against source verification: Is the publisher verified? Is the source code available? When was it last updated? Smaller, actively maintained extensions from known publishers often present less risk than popular extensions from anonymous developers. This approach mirrors AppSec maturity practices applied at the developer workstation level.
Package manager selection: Evaluate security posture alongside features. If your organization runs npm-dependent pipelines, understand what npm will and won't protect you from. Consider whether migration to a more actively defended package manager belongs on your roadmap. SCA tools can help identify these risks systematically.
Environment isolation: Development environments should be security boundaries, not open pathways to production. Limit what credentials exist on developer machines. Segment access so a compromised workstation doesn't provide direct routes to production systems.
Monitoring: Track extension installations across your development team. Monitor for unexpected network connections from development environments. Treat unusual activity from developer machines with the same seriousness as anomalies in production.
The Attack Surface Will Grow
AI coding assistants are becoming standard developer tools. Each one represents another trust relationship, another data flow, another potential exfiltration channel. The attack surface isn't shrinking.
Your toolchain deserves production-grade security rigor. Audit your installed extensions. Evaluate your package manager's security posture. Implement environment isolation. Monitor for anomalies.
Do you have extension allowlisting? Marketplace source verification? Isolated development environments?
These aren't paranoia anymore. They're hygiene.