Jaya Gupta and Ashu Garg of Foundation Capital, just published a thesis that deserves attention: "AI's Trillion-Dollar Opportunity: Context Graphs."
Their argument: The last generation of enterprise software became trillion-dollar platforms by becoming systems of record. Salesforce for customers. Workday for employees. SAP for operations. The next generation? Systems of record for decisions.
Not what data exists. Why it was acted on. Here's the insight that matters for security leaders:
"Agents don't just need rules. They need access to the decision traces that show how rules were applied in the past, where exceptions were granted, how conflicts were resolved, who approved what."
Read that again, now let's apply it to AppSec.
What AppSec Has Today: Systems of Detection
Your security stack is full of systems of record:
• SAST tools record what vulnerabilities exist
• SCA tools record what dependencies are outdated
• ASPM platforms record how findings are prioritized
• JIRA records what tickets were assigned
But here's the critical gap: None of them capture why security decisions were made.
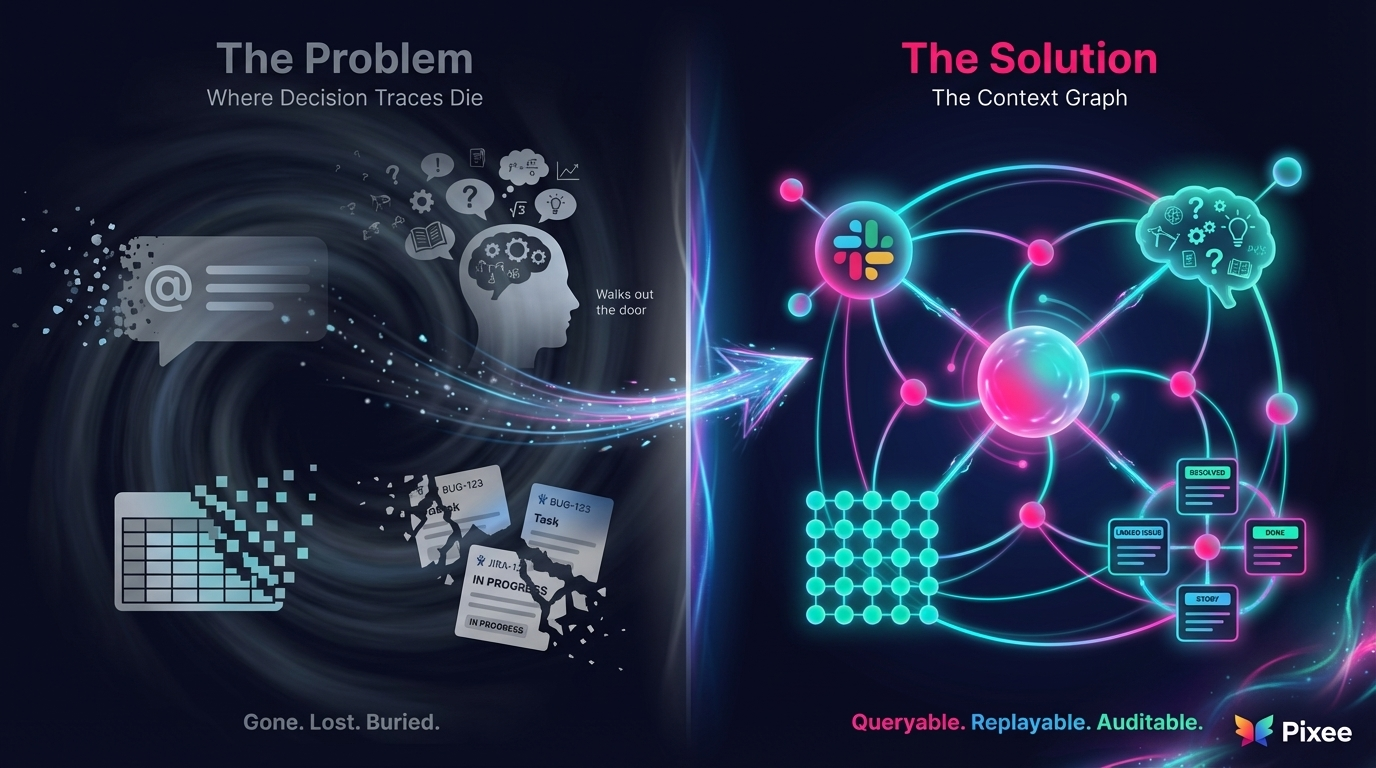
The AppSec context graph addresses this fundamental limitation in how security automation platforms operate today. When your team deprioritizes a finding, where does the reasoning go? Slack thread. Gone.
When a developer rejects a suggested fix, where does that learning go? Individual memory. Gone.
When you suppress 80% of scanner findings as false positives, where's the evidence trail? Spreadsheet. Lost.
The decision trace—the context that explains WHY something was triaged out, WHY a fix was rejected, WHY a precedent applies—currently lives in people's heads. And it walks out the door when they leave.
The Mirror Dimension: Pixee's AppSec Context Graph
Foundation Capital calls it a "context graph." I think of it as a mirror dimension—a parallel reality where every security decision leaves a trace, your security product security knowledge lives on and your context is focused from a security-minded perspective.
Your scanners show you the primary dimension: what vulnerabilities exist right now. Current state. A snapshot. The mirror dimension shows you something different: the decision history that explains how you got here. Why findings were triaged out. What evidence justified each suppression. Which precedents applied. What fixes your developers trusted—and which ones they rejected. One dimension tells you what's broken. The other tells you how your organization actually thinks about security.
When we built Pixee, we didn't realize we were building this mirror dimension. We thought we were building an automation platform. But the architecture we ended up with is exactly what Foundation Capital describes:
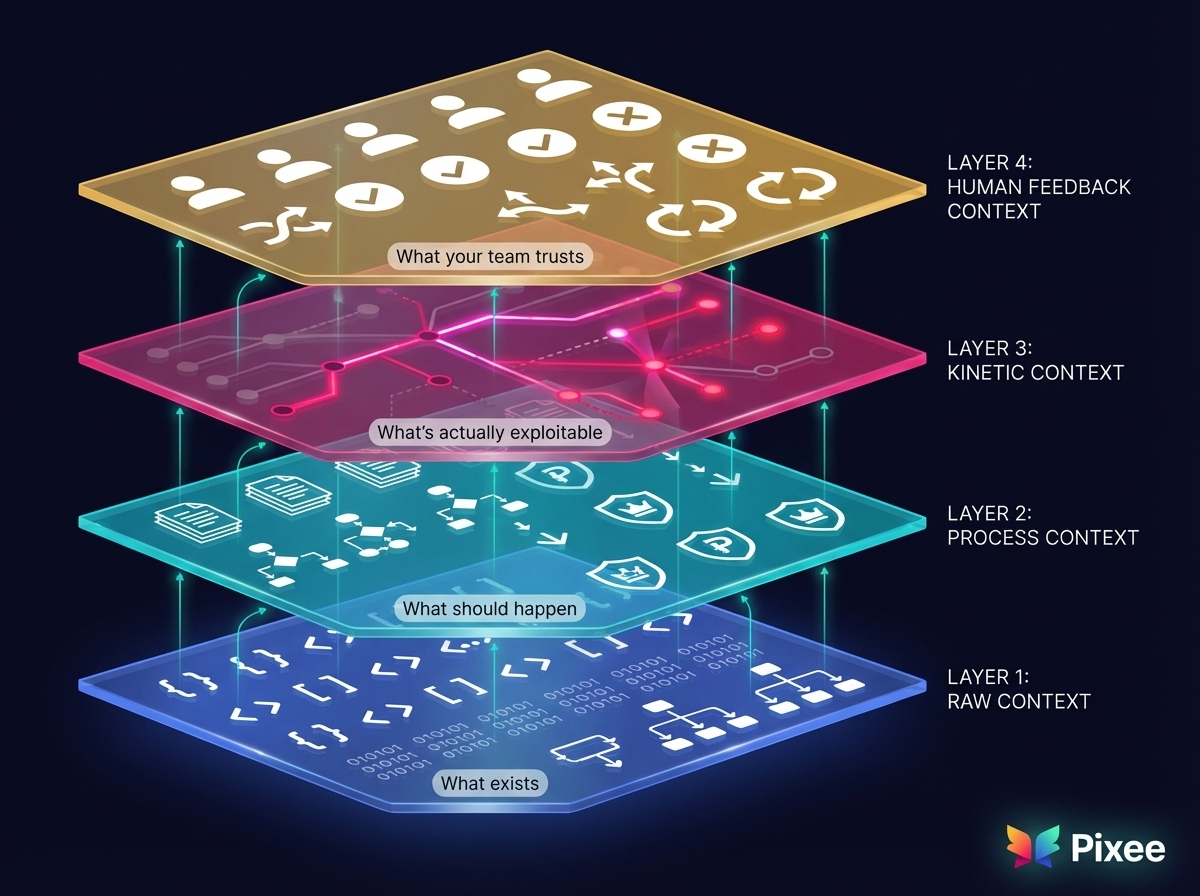
Raw Context: Code, scanner findings, dependencies, configurations. The "what exists" layer.
Process Context: Your security policies, architectural patterns, governance rules, team conventions. The "what should happen" layer.
Kinetic Context: Exploit verification, reachability analysis, cross-scanner correlation. The layer that proves what's actually exploitable vs. what's theoretically vulnerable.
Human Feedback Context: Developer merge/reject patterns, organizational preferences, historical precedents. The layer that captures what your team actually trusts.
Every time we triage a finding, we create a decision trace: What inputs were evaluated. What policy applied. What evidence was used. What precedent was referenced. That trace doesn't die in Slack. It becomes queryable. Replayable. Auditable.
That's the context graph. That's your Pixee mirror dimension.
Why Context Graphs Matter for CISOs
Foundation Capital identifies a problem enterprises know intuitively:
"Exception logic lives in people's heads. Precedent from past decisions isn't stored. Approval chains happen outside systems."
Sound familiar?
An AppSec context graph that captures decision traces solves this institutional knowledge problem. In AppSec, this manifests as:
• New security engineers spending months learning tribal knowledge — "Oh, we always suppress that finding because of the WAF configuration. Nobody documented it."
• Audits requiring manual reconstruction of suppression decisions — "Why did we mark 40,000 findings as false positives? Let me dig through two years of JIRA comments."
• The same false positive getting re-triaged every quarter — Because there's no institutional memory that this code path is behind three authentication layers and has been validated as unexploitable.
• No learning from what fixes developers accept vs. reject — That 76% merge rate we achieve? It comes from capturing decision traces about what fixes work in YOUR codebase and feeding that back into future suggestions.
A context graph that captures decision traces isn't just automation. It's institutional security knowledge—organizational memory that doesn't walk out the door when people leave.
The Mirror Dimension Advantage
Here's what changes when your security program has a context graph:
Before: Scanner finds SQL injection. Analyst investigates. Finds it's in dead code behind three auth layers. Closes ticket. Reasoning lives in analyst's head.
After: Scanner finds SQL injection. Context graph shows this code pattern was evaluated 47 times across the organization. Reachability analysis confirms it's unexploitable. Evidence trail is queryable. Next time this pattern appears, the decision is automatic—with full audit trail.
Before: Developer rejects AI-generated fix. Feedback disappears into PR comments.
After: Developer rejects fix. Context graph captures the rejection pattern. System learns that YOUR team prefers a different error-handling approach. Future fixes adapt. Merge rate improves because the mirror dimension remembers.
Before: New CISO asks "Why is our backlog 100,000 findings if we've been running security tools for years?"
After: The AppSec context graph shows exactly how 80,000 findings were validated as false positives with evidence, creating a decision audit trail. When they were validated, and what policies governed the decisions. Board gets a defensible answer, not a spreadsheet archaeology project.
The Strategic Implication
Foundation Capital poses a question:
"The core question isn't whether existing systems of record survive. It's whether entirely new ones emerge—systems of record for decisions, not just objects."
For AppSec, I'd reframe it:
The question isn't whether SAST and SCA tools survive. They will. The question is whether a new layer emerges—a context graph for security decisions—that captures the decision logic between "vulnerability found" and "code shipped." That layer becomes the mirror dimension of your security program. And whoever builds that mirror dimension owns the most valuable artifact in AppSec: the institutional knowledge of how your organization actually makes security decisions. Detection tells you what's wrong. Prioritization tells you what matters.
The context graph tells you why something was fixed—or why it wasn't. That "why" is the trillion-dollar insight.
What This Means in Practice
The incumbents can't build the context graph for the same reason Foundation Capital identifies: they're not in the decision path.
Scanners see findings. They don't see triage decisions.
ASPM platforms see prioritization. They don't see the exception logic that justifies suppression.
Ticketing systems see assignments. They don't see why developers reject fixes.
The context graph requires sitting in the execution path—where the decision happens. That's where the trace gets captured. That's where the mirror dimension gets built.
For enterprise security leaders, the question becomes: Who is building your context graph?
Right now, the answer for most organizations is: nobody. The decision traces exist, but they're scattered across Slack, JIRA comments, individual memory, and spreadsheets that get deleted when someone leaves.

That's the gap waiting to be closed.
The Foundation Capital article is worth reading in full. They identify patterns across RevOps, FinOps, and enterprise automation that mirror exactly what we're seeing in AppSec. The shift from systems of record to systems of decision is real—and security is no exception.






