CVE Had a Near-Death Experience. Europe's Response: Build Their Own.
On January 7, 2026, the European Union launched db.gcve.eu, the Global Cybersecurity Vulnerability Enumeration database. Europe's answer to America's monopoly on vulnerability intelligence.
This marks a shift toward a multi-polar vulnerability intelligence ecosystem. Security teams now have two authoritative sources to track, correlate, and integrate.
Why Europe Built Its Own
In April 2025, funding disputes involving DOGE and MITRE threatened a complete blackout of CVE data. The backbone of virtually every vulnerability management program on the planet nearly went dark.
European organizations subject to NIS2 directive requirements suddenly faced losing their primary compliance data source overnight. Organizations realized they had built security programs on infrastructure controlled by a single foreign government. For a continent focused on digital sovereignty, from GDPR to the Digital Services Act, this dependency became untenable.
Rather than creating a backup system, the EU designed a decentralized vulnerability intelligence network aggregating data from 25+ European CSIRTs, vendor advisories, and research organizations.
Technical Architecture: Decentralization vs. Central Control
The US CVE system relies on MITRE as the central numbering authority. GCVE implements a "decentralized Global Numbering Authority (GNA) model." Multiple European authorities can assign identifiers simultaneously.
Under the traditional CVE model, critical vulnerabilities can wait weeks for identifier assignment. The process reflects primarily US-centric priorities.
GCVE's decentralized approach lets the German BSI, France's ANSSI, and other European agencies issue identifiers based on regional expertise. European organizations get faster access to vulnerability intelligence relevant to their threat landscape without waiting for US-based analysis.
The technical implementation aggregates data through standardized APIs aligned with ISO/IEC 29147 and CVSS.
Immediate Impact: What Changes for Security Teams
If you're running vulnerability scans and reporting compliance metrics based solely on CVE data, you now have a gap in intelligence coverage. This complexity compounds the security backlog crisis many organizations already face.
European software vendors contribute approximately 30-35% of global vulnerability disclosures. These organizations are now likely to prioritize GCVE reporting, potentially creating lag times before vulnerabilities appear in US databases.
The 24-48 hour gap: European vendors are publishing vulnerability advisories to GCVE before they appear in MITRE's queue. For organizations with significant European operations, that gap represents real exposure.
Security tools built around CVE identifiers (Nessus, Qualys VMDR, Phantom) now need to normalize data across multiple identifier systems.
Severity scoring adds complexity. While both systems use CVSS as a baseline, regional differences can produce different scores for identical vulnerabilities. European-focused vulnerabilities might receive higher priority in GCVE than CVE.
For organizations subject to European regulatory frameworks: The NIS2 directive references "authoritative vulnerability databases" without specifying CVE exclusively. Legal teams are already advising European subsidiaries to demonstrate GCVE coverage.
Strategic Implications: Fragmentation or Resilience?
Does multiple vulnerability databases create dangerous fragmentation, or build essential resilience?
The fragmentation risk: Security teams already struggle with alert fatigue and triage burden. Another database with potentially inconsistent identifiers, timing, and severity assessments could worsen signal-to-noise problems. As we've documented, organizations already spend 60-80% of security team time on alert triage rather than strategic work, exacerbating CISO burnout.
The resilience argument: The April 2025 CVE funding crisis demonstrated single-source dependency risk. A vulnerability intelligence ecosystem with multiple authoritative sources is more robust against manipulation, funding disruption, or technical failure.
The European model brings regional expertise that CVE historically lacked. European cybersecurity agencies have deep knowledge of local software vendors and threat actor behaviors that don't translate through US-centric frameworks.
Early evidence suggests benefits may outweigh costs. Organizations implementing dual-source tracking during GCVE's beta report 15-20% improvement in vulnerability coverage for European software components.
Implementation Roadmap
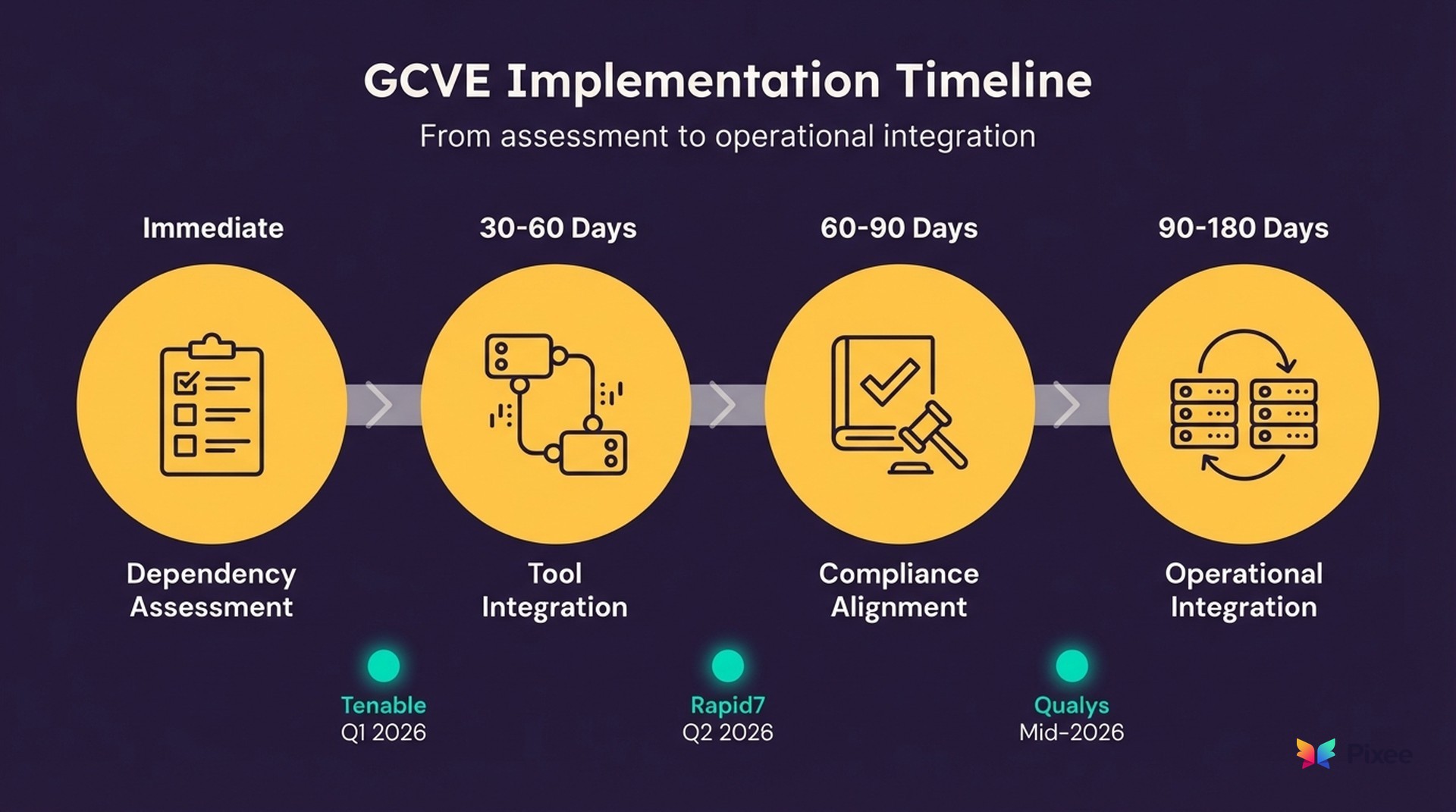
Phase 1: Dependency Assessment (Immediate)
Audit your CVE dependencies. Map every tool, process, and compliance requirement relying on CVE data. Include vulnerability scanners, patch management, security orchestration playbooks, and incident response procedures.
CVE identifiers are embedded in automated ticketing systems, board reporting templates, and more. Most organizations don't realize the depth until they try adding another data source.
Phase 2: Tool Integration Planning (30-60 days)
Major vulnerability management platforms are announcing GCVE integration timelines:
• Rapid7 InsightVM: Q2 2026
• Tenable.io: Beta Q1 2026
• Qualys VMDR: Mid-2026
For custom tooling, plan 3-6 months of development work.
Phase 3: Compliance Alignment (60-90 days)
Clarify GCVE requirements with legal teams. While no European regulation explicitly mandates GCVE coverage yet, organizations demonstrating "reasonable care" will increasingly need to show awareness of all authoritative sources.
Phase 4: Operational Integration (90-180 days)
Begin parallel tracking of CVE and GCVE data for critical systems. Start with European operations. Develop normalization procedures for vulnerabilities appearing in both databases with different identifiers or severity scores. Implementing automated remediation workflows becomes increasingly critical as you manage multiple data sources.
Vendor Response: Multi-Source Integration
The security tool ecosystem is adapting. Snyk announced comprehensive GCVE integration in December 2025. Most major vendors plan GCVE support by mid-2026.
Integration approaches by category:
• Vulnerability Scanners: GCVE as parallel data source with correlation logic for deduplication
• Security Orchestration: Normalization engines creating unified vulnerability records
• Risk Management: Scoring frameworks considering both CVE and GCVE severity with regional weighting
• Compliance Platforms: Reporting capabilities demonstrating coverage across authoritative sources
Looking Ahead: Global Vulnerability Intelligence Fragmentation
The GCVE launch likely represents the beginning of vulnerability intelligence diversification. Other regions are watching.
Asia-Pacific cybersecurity agencies have discussed similar initiatives as US-China technology tensions create pressure for independent security infrastructure. Japan's NISC and Australia's ACSC have published research on regional vulnerability intelligence requirements.
The US National Cybersecurity Strategy emphasizes American leadership in global standards, while European policy documents reference "strategic autonomy" in digital infrastructure. Continued divergence seems likely.
Long-term: Multiple authoritative databases could influence vulnerability research incentives, disclosure practices, and coordination mechanisms. Researchers might prioritize disclosure to databases offering faster publication or better economic incentives.
Conclusion
The GCVE launch brings both challenges and opportunities for security leaders.
Challenges: More data sources to manage, more tools to integrate, more compliance requirements to navigate.
Opportunities: Redundancy against single points of failure, regional expertise in global threat intelligence, more comprehensive coverage of diverse technology ecosystems.
As other regions consider similar initiatives, the question becomes how quickly security teams can build multi-source vulnerability intelligence capabilities.