From 2,000 Alerts to 50 Fixes: The Triage Automation Playbook

A security leader at a Fortune 500 bank put it bluntly in a recent conversation: "50, 60, 70, maybe 80 percent of our findings are false positives, not important, or don't need to be fixed. And the triage effort is entirely manual. It requires expertise we don't have enough of."
This isn't an outlier. It's the norm.
Most application security teams aren't spending their time fixing vulnerabilities. They're drowning in triage—the exhausting, manual process of determining which of their thousands of scanner findings actually matter. In fact, 78% of security alerts go completely uninvestigated due to volume overload.
The dirty secret of AppSec is that the majority of "work" isn't remediation. It's figuring out what's real, what's relevant, and what can wait.
The industry is finally starting to name this problem. Bugcrowd launched an "AI Triage Assistant" in December 2025, explicitly targeting the triage bottleneck. At Pixee, we built the Context Platform with triage automation as its foundation—because you can't be good at fixing without being good at understanding what needs to be fixed.
This post isn't another "triage is hard" lament. It's a systematic framework for thinking about triage automation. Whether you build capabilities internally, evaluate vendors, or hybrid your approach by the end you should have a better understanding of why most triage approaches fail, plus a three-part framework and a five-step playbook for implementating smarter triage.
The 3-Part Triage Framework
Effective triage requires three distinct decisions, each demanding different intelligence.

Category 1: False Positives (The Scanner Was Wrong)
The vulnerability doesn't actually exist in your code. The scanner pattern-matched something that looks like a problem but isn't.
This happens constantly:
• A SAST tool flags a potential SQL injection, but the input is actually sanitized three functions upstream
• An SCA scanner reports a critical CVE in a dependency, but your code never calls the vulnerable function
• A DAST scan identifies a potential XSS, but the response was actually properly encoded
False positive detection requires intelligence that understands code paths, data flows, and actual reachability—not just pattern matching. When a scanner says "this dependency has a vulnerability," the real question is: "Does our code actually use the vulnerable component in a vulnerable way?" This is where reachability analysis becomes essential—determining whether vulnerable code is actually callable in your specific environment.
False positives typically account for 40-50% of findings in mature organizations. In less mature environments with default scanner configurations, it can be even higher.
Category 2: Won't Fix (Real But Acceptable)
The vulnerability genuinely exists, but business context makes it an acceptable risk.
This is the category scanners can't see. Take the case of the same critical SQL injection. In the first case the vuln exists in an internal admin tool, accessible only behind a corporate VPN with MFA and IP allowlisting. In the second case this vulnerability shows up in a public-facing checkout API. Both are "real" vulnerabilities. Only one demands immediate action.
Proper won't-fix decisions require understanding your environment. That's things like service classification (internal vs. external), compensating controls (WAF rules, network segmentation), authentication requirements, and organizational risk tolerance. None of this information exists in scanner output.
This category typically represents 20-30% of findings that could in theory be de-prioritized.
Category 3: Risk Re-Scoring (Real But Over-Rated)
The vulnerability exists and needs attention, but not at the severity the scanner assigned.
CVSS scores vulnerabilities in theoretical isolation. A CVSS 9.8 assumes worst-case conditions: network accessible, no authentication required, complete system compromise possible. But your environment isn't worst-case. That "critical" vulnerability might exist in a containerized service with no shell access, behind three layers of authentication, on an isolated network segment. Industry research shows 88% of "Critical" CVEs aren't actually exploitable in real-world context.
Risk re-scoring doesn't dismiss findings—it contextualizes them. A containerized, network-isolated, authenticated-only vulnerability is still a vulnerability. It's just not a "drop everything" emergency competing with findings that are actively exploitable from the internet.
This category typically accounts for 10-20% of findings—real issues that warrant tracking and eventual remediation, but not at the priority their raw CVSS scores suggest.
The Framework Applied
When you apply all three categories systematically:
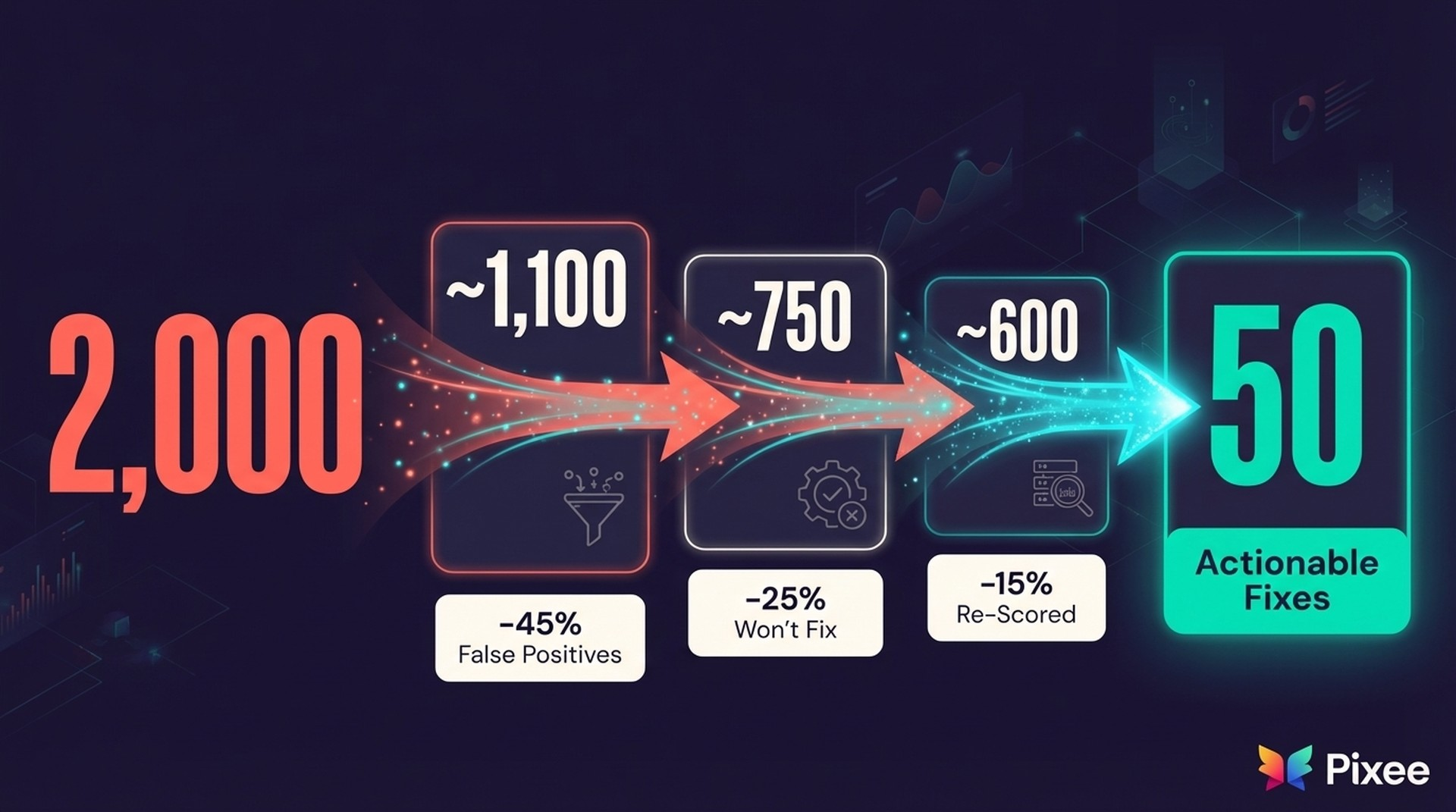
• Start with 2,000 findings
• Remove 40-50% false positives → 1,000-1,200 remain
• Remove 20-30% won't-fix → 700-960 remain
• Re-score 10-20% to lower priority → 560-860 for eventual attention
• Truly urgent, exploitable, needs-immediate-action: ~50-200 findings
That's the journey from 2,000 to 50. Not by ignoring risk, but by finally having the intelligence to distinguish signal from noise.
The 5-Step Triage Automation Playbook
Understanding the framework is step one. Implementing it is where value gets created. Here's the playbook.

Step 1: Unified Visibility
Before you can automate triage decisions, you need one place to see all findings.
What this requires:
Aggregate findings from all scanners into a unified format. Most organizations run multiple tools—SAST, DAST, SCA, container scanning, cloud security posture. Each generates findings in different formats, with different severity scales, using different terminology.
Normalize severity ratings. "Critical" in Tool A doesn't equal "Critical" in Tool B. Without normalization, you can't compare or prioritize across sources. Organizations with 65+ security tools face this challenge daily.
Deduplicate cross-scanner findings. The same CVE flagged by three different tools isn't three problems—it's one problem reported three times. Without deduplication, your backlog is artificially inflated, and you waste time investigating the same issue multiple times.
The arbitration problem: When different scanners disagree, who wins? A security architect at a global bank described spending "hours determining which tool to trust" on conflicting findings. One scanner says Critical, another says Medium, a third says False Positive. Automation starts with eliminating this arbitration tax.
The question to ask yourself: How much time does your team spend context-switching between dashboards? If the answer is "hours per week," unified visibility pays for itself before you automate anything else.
Step 2: False Positive Intelligence
If 40-50% of findings are false positives, the highest-ROI automation eliminates them before human review.
The intelligence required:
For SCA (dependency vulnerabilities):
Reachability analysis asks: Is the vulnerable function actually called by your code? A dependency can contain a vulnerability, but if your application never invokes the vulnerable code path, the risk is theoretical, not practical.
Version validation confirms: Are you actually running the vulnerable version range? Scanners sometimes flag CVEs for version ranges you're not actually using.
Transitive depth matters: A vulnerability in a direct dependency you explicitly chose is different from one buried six layers deep in a transitive dependency you've never heard of.
For SAST (code vulnerabilities):
Data flow analysis determines: Can untrusted input actually reach this sink? Many SAST findings flag potential injection points that, upon analysis, can never receive untrusted data.
Dead code detection asks: Is this code path even executable in production? Vulnerabilities in unreachable code aren't vulnerabilities—they're noise.
The key insight: These are deterministic checks. A vulnerability either is or isn't reachable. Your code either does or doesn't call the function. This is perfect for automation—no judgment required, just analysis.
The trap to avoid: Simple severity filtering isn't false positive detection. Hiding "Low" findings just hides findings—it doesn't determine whether "Critical" findings are real. You can filter out every Low and Medium finding and still drown in false-positive Criticals.
The question to ask yourself: What percentage of findings sent to developers turn out to be false positives? If developers are dismissing most alerts, you have a false positive problem masquerading as a prioritization problem.
Step 3: Business Context Awareness
"Won't fix" decisions require understanding your environment—something scanners fundamentally can't provide. But most business context is stable and encodable.
Context categories that matter:
Service classification:
Internal-only services have different risk profiles than customer-facing ones. Admin tools behind corporate VPN aren't equivalent to public API endpoints. Batch processing systems that run overnight aren't the same as real-time transaction systems handling customer data.
Compensating controls:
WAF rules that block specific exploit patterns change the exploitability of web vulnerabilities. Network segmentation that limits blast radius affects the impact of any compromise. Authentication layers—especially MFA—change what "unauthenticated access" actually means for internal services.
Lifecycle status:
Services scheduled for deprecation in 90 days warrant different investment than services with five-year roadmaps. Legacy systems with formally accepted technical debt shouldn't generate surprise findings. Greenfield projects might have stricter standards than brownfield systems with known constraints.
Implementation pattern: Create a service registry with security metadata. When findings come in, auto-enrich with context. "Critical SQLi in internal-admin-tool behind-vpn with-mfa" is fundamentally different from "Critical SQLi in public-checkout-api"—but without context enrichment, most tools treat them identically.
The trap to avoid: Manual tagging doesn't scale. If every finding requires a human to remember "oh, that service is internal-only," you haven't automated—you've added steps. The goal is encode-once, apply-automatically.
The question to ask yourself: Can you encode your risk decisions once and have them apply automatically to new findings? The best security teams make risk decisions explicit and systematic, not ad-hoc and tribal.
Step 4: Exploitability Context
CVSS assumes worst-case isolation. Your environment has context.
Factors that change real-world exploitability:
Attack surface exposure:
Is this service internet-facing or internal-only? Does accessing the vulnerable endpoint require authentication or is it anonymous? How many network hops and security controls exist between an attacker and the vulnerable code?
Exploit availability:
Is there a proof-of-concept exploit public? Has the vulnerability been weaponized for real attacks? Is it listed on CISA's Known Exploited Vulnerabilities catalog, meaning it's actively being used in the wild?
Environmental barriers:
Does the container have shell access, or is it distroless? Is the filesystem read-only? Is the execution environment sandboxed in ways that limit what a successful exploit could accomplish?
The scoring principle: Don't replace CVSS—augment it.
CVSS 9.8 + internal-only + no-public-exploit + containerized = effective risk much lower than the raw score suggests.
CVSS 6.5 + internet-facing + actively-exploited + no-compensating-controls = effective risk much higher than the raw score suggests.
The goal isn't to dismiss high CVSS scores. It's to ensure a containerized, network-isolated, authenticated-only CVSS 9.8 doesn't outprioritize an internet-facing, actively-exploited CVSS 6.5 just because 9.8 > 6.5.
The trap to avoid: Building exploitability scoring from scratch requires ongoing threat intelligence investment most organizations can't sustain. Tracking which vulnerabilities have public exploits, which are actively exploited, and which have been weaponized is a full-time job. Look for solutions that maintain this intelligence for you.
The question to ask yourself: Would a Critical vulnerability in a sandboxed container with no network access still be treated as Critical by your current process? If yes, you're likely over-remediating low-risk findings while under-resourcing high-risk ones.
For more on why severity scores mislead, see our analysis of the security budget-backlog disconnect.
Step 5: Remediation Readiness
After proper triage, you're left with findings that are: real (not false positives), relevant (not won't-fix), and properly prioritized (risk re-scored). Now what?
What changes when triage is solved:
Developer trust returns.
When every alert sent to developers is real and relevant, they stop ignoring security tools. One security leader described the trust collapse: "When the well is already poisoned, it's very hard to change developers' minds anymore." Past false positives trained developers to dismiss everything. Proper triage is how you rebuild that trust.
Remediation becomes measurable.
"50 vulnerabilities fixed this sprint" finally means something when you're not counting false positives and won't-fixes in that number. You can track actual security improvement, not just activity.
Automation becomes viable.
Automated remediation—AI-generated fixes, automated dependency updates, code hardening—works when you're certain the finding is real and relevant. Automating fixes for false positives just creates churn and erodes the developer trust you're trying to build.
The connection: Triage automation and remediation automation aren't separate problems—they're sequential. You can't reliably automate fixes for findings you haven't validated. And there's limited value in validating findings you can't act on efficiently. This is why organizations reaching Level 4 AppSec maturity invest in both capabilities together.
The question to ask yourself: When you correctly identify a real vulnerability, how long until fixed code ships? If triage is fast but remediation is slow, you've moved the bottleneck, not solved it.
For how triage and remediation connect in practice, see Introducing Pixee for SCA.
The Triage Transformation
The security industry spent two decades optimizing detection. We have more scanners finding more vulnerabilities than ever before. Mission accomplished on finding things.
The bottleneck moved. It's been sitting at triage for years, but we kept buying more scanners anyway.
Triage isn't a necessary evil to endure—it's a systematic problem with systematic solutions. The three-part framework (false positives, won't fix, risk re-scoring) isn't just conceptual—each category maps to specific, automatable capabilities.
From 2,000 alerts to 50 fixes isn't about ignoring risk. It's about finally having the intelligence to know which 50 actually matter.
The market is responding—not with more scanners, but with intelligence layers designed to make sense of what scanners already find. The question isn't whether triage automation is coming—it's whether you'll be early or late.
Your AppSec team is currently spending 80% of their time not fixing things. That can change. The framework exists. The playbook is clear. The only remaining question is when you start.
Ready to implement? See our 4-step plan to reduce your security backlog by 91%.

