77% of your application code didn't come from your developers. It came from open source dependencies, third-party libraries, and inherited components you have limited visibility into—and even less control over.
This code sits in your production environment right now, with known vulnerabilities that attackers are actively exploiting while you drown in alerts you can't effectively prioritize or fix.
The numbers tell the story:
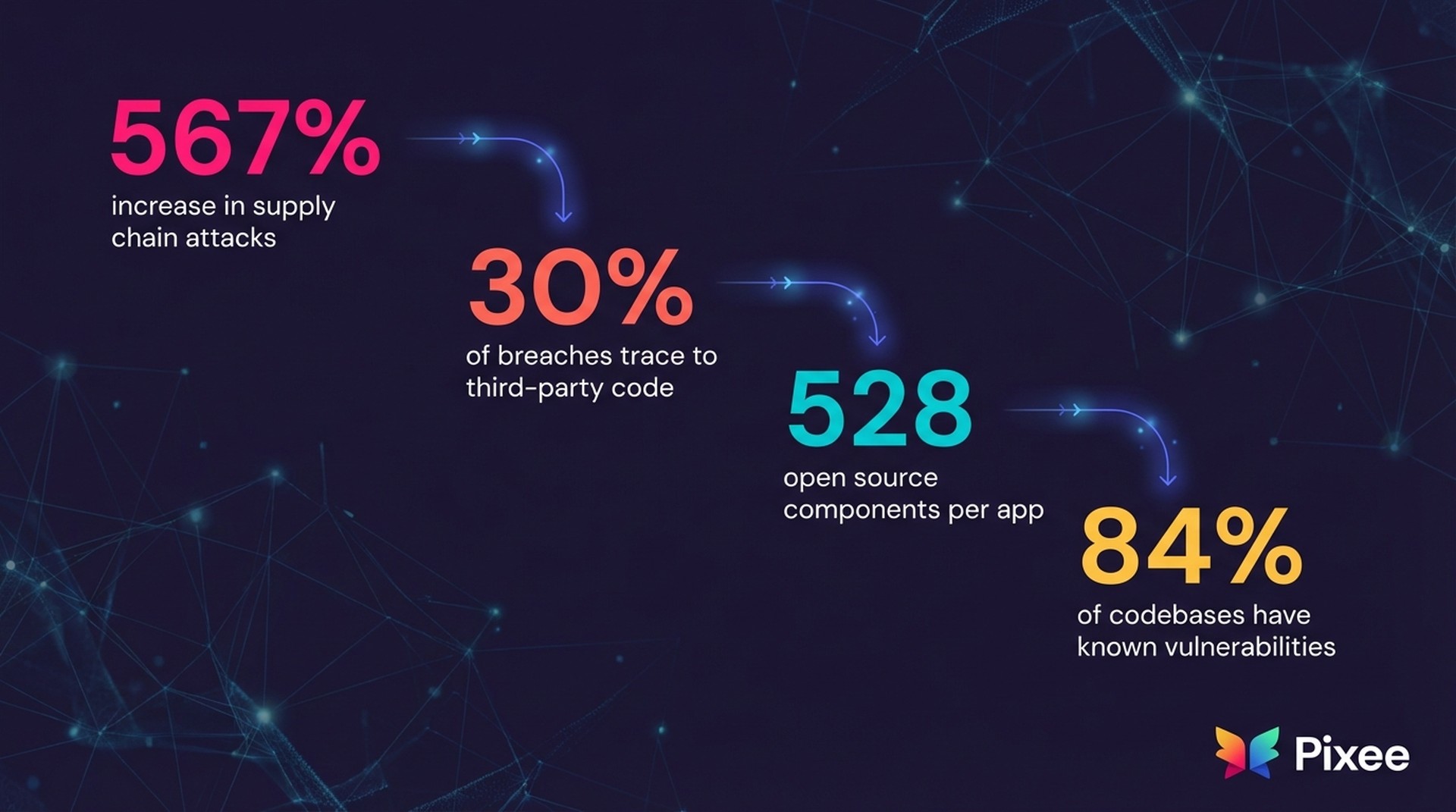
• Supply chain attacks increased 567% in 2025, with attackers averaging 12 minutes to compromise supply chains
• 30% of all breaches now trace to third-party vulnerabilities—up from 15% in 2024
• The average enterprise application contains 528 open source components
• 84% of codebases contain at least one known vulnerability
Traditional SCA tools are making the problem worse.
By the Numbers: The SCA Reality
Modern software development has fundamentally changed. The days of building everything from scratch are long gone. Open source components now comprise 70-90% of most commercial applications, enabling faster development cycles and reducing time-to-market.
But this efficiency comes with security debt most organizations are only beginning to understand.
The vulnerability landscape is exploding:
• 48,185 CVEs published in 2025—that's 115 new vulnerabilities disclosed DAILY, a 21% increase from 2024
• The average time between vulnerability disclosure and active exploitation has dropped to 15 days
• The average time-to-fix for most organizations remains 69 days
Research from Rezilion found that only 9.5% of published CVEs actually have known exploits.
Why Your SCA Tools Create More Problems Than They Solve
If you're a CISO reading this, you've likely invested heavily in Software Composition Analysis tools. You probably run multiple scanners—maybe Snyk, Mend, Veracode, or others. Despite this investment, your security backlog keeps growing.
They're solving the wrong problem. But these are the 4 that really matter:

Problem #1: 88% of Your SCA Alerts Don't Matter
Traditional SCA tools scan everything and flag everything. Industry data shows false positive rates of 71-88% across most vulnerability scanners.
In practice: Your SCA tool identifies 2,847 "vulnerabilities" in your latest scan. You have bandwidth to investigate maybe 50 per week. Even working on nothing else, it would take 57 weeks to clear the backlog—assuming no new code ships in the meantime.
Problem #2: CVSS Scores Don't Reflect Your Reality
The Common Vulnerability Scoring System (CVSS) was designed to provide standardized severity ratings. JFrog's research revealed a critical flaw: 88% of "Critical" CVEs aren't actually critical in most environments.
CVSS scoring doesn't understand:
• Your specific code execution paths
• Your authentication boundaries
• Your network segmentation
• Your defensive layers
A "Critical" SQL injection vulnerability in a library your application never calls isn't critical for you—it's noise.
Problem #3: The Scoring System Broke
Even when CVSS scores were useful, they had limitations. Now they're not even available.
93% of new CVEs published in 2025 lack NVD analysis. Over 20,000 vulnerabilities are waiting in queue for severity scoring—a backlog that grows by 115 CVEs daily.
If you're relying on CVSS for prioritization, you're flying blind for 9 out of 10 new vulnerabilities.
Problem #4: The Manual Remediation Bottleneck
Even when you correctly identify a real vulnerability that needs fixing, the remediation process stalls. Surveys show you spend 60-80% of your time on vulnerability triage rather than strategic security work.
The typical workflow:
1. Identify vulnerable dependency
2. Create ticket for development team
3. Developer researches the issue (if they have time)
4. Attempts to upgrade dependency
5. Discovers upgrade breaks functionality
6. Spends hours debugging compatibility issues
7. Either ships a risky workaround or leaves vulnerability unfixed
Meanwhile, your backlog grows by dozens of new issues daily.
The Real Cost: More Than Breach Cleanup
SCA costs more than breach cleanup. IBM's 2024 Cost of a Data Breach Report found that the average breach now costs $4.88 million.
But look at what else you're paying:
Your Team's Time:
• 2-3 security engineers spending 60-80% of time on manual triage
• Average loaded cost: $180K per engineer per year
• Opportunity cost: $216K-$324K annually in displaced strategic work
Developer Productivity:
• Average 2.3 hours per developer per week dealing with security findings
• For a 50-person engineering team: 115 hours weekly = $312K annually in lost productivity
• Context switching reduces overall development velocity by 15-25%
When you can't keep up with vulnerability remediation, you make dangerous trade-offs:
• Delaying dependency updates (creating larger future upgrade challenges)
• Implementing workarounds instead of proper fixes
• Accepting security exceptions that compound over time
The $8.5M Trust Wallet npm supply chain compromise in 2025 showed the real-world cost when dependency vulnerabilities are exploited—and that was a single package in a single ecosystem.
What You Can't Do While Triaging Alerts
The most damaging cost is what you aren't able to focus on while drowning in SCA triage:
• Architecture security reviews for new systems
• Threat modeling for critical applications
• Security automation and tooling improvements
• Proactive threat hunting and detection engineering
• Security training and culture building
Developer Morale: The Unseen Cost
33% of developers now HOPE vulnerabilities won't be found during scans—up from 15% the previous year. This isn't laziness. It's resignation.
When every sprint brings 50+ security tickets, half of which are false positives, and the other half require days of investigation, developers stop engaging. Security becomes something to route around, not collaborate on.
This erosion of security culture is harder to measure than breach costs, but it's the foundation of long-term security posture.
What Changes When You Focus on Reachability
The solution isn't more scanning or more alerts. It's understanding which vulnerabilities actually matter in your environment—and fixing them without breaking your applications.
Reachability Analysis: Focus on What Matters
Instead of treating every CVE equally, modern SCA approaches use reachability analysis to determine which vulnerabilities are actually exploitable in your specific codebase.
This means analyzing:
• Code execution paths: Is the vulnerable function actually called?
• Data flow: Can user input reach the vulnerable code?
• Authentication context: Are vulnerable endpoints protected?
• Network exposure: Is the vulnerable service accessible to attackers?
Research from Snyk shows that reachability analysis reduces actionable vulnerabilities by 85% while maintaining the same security coverage.
Automated Remediation: Generate Fixes That Work
Automated remediation goes beyond simple dependency updates. Modern approaches:
• Analyze your specific codebase to understand usage patterns
• Generate contextually appropriate fixes (updates, patches, or code changes)
• Test fixes against your build and test suites
• Provide pull requests developers can review and merge
Unified Visibility: Single Pane of Truth
Rather than managing outputs from multiple scanners, leading organizations consolidate SCA findings into a unified remediation layer that:
• Deduplicates findings across multiple tools
• Provides consistent prioritization based on actual risk
• Tracks remediation progress across all applications
• Integrates with existing development workflows
This reduces cognitive load on both security and development teams while ensuring nothing falls through the cracks.
Four Things to Start Doing This Quarter
If you're ready to move beyond the alert treadmill:
Weeks 1-4: Establish Baseline and Prioritize
Audit Your Current State
• Inventory all SCA tools currently in use
• Calculate current false positive rates and triage time
• Measure developer satisfaction with security tooling
• Document current vulnerability backlog size and age
Implement Risk-Based Prioritization
• Focus on vulnerabilities in code paths that handle user input
• Prioritize internet-facing applications over internal tools
• Consider business criticality of affected applications
• Use exploit availability (not just CVSS) for severity ranking
Weeks 5-8: Reduce Noise and Improve Signal
Deploy Reachability Analysis
• Implement tools that understand your actual code execution paths
• Filter out vulnerabilities in unused dependencies or unreachable code
• Establish SLAs based on actual exploitability: 7 days for reachable critical, 30 days for reachable high
Automate Routine Remediation
• Identify patterns in successful vulnerability fixes
• Automate dependency updates for non-breaking changes
• Generate pull requests for common vulnerability patterns
• Measure and optimize merge rates for automated fixes
Weeks 9-12: Scale and Optimize
Integrate with Development Workflow
• Embed security fixes into regular development cycles
• Provide developers with context and remediation guidance
• Track fix velocity as a key security metric
• Celebrate successful security improvements
Measure and Iterate
• Track mean-time-to-remediation by vulnerability type
• Monitor developer productivity impact
• Measure security team time allocation (strategic vs. tactical)
• Adjust prioritization based on actual attack patterns
Moving From Reactive to Proactive
With the right approach, dependencies enable faster development while maintaining security.
The question isn't whether you can afford to implement modern SCA management. It's whether you can afford not to.
If you're managing SCA findings at scale, context-aware reachability analysis and automated remediation change the game.