Add exploitability verification to your existing scanners. Value in days, not months.
Third-party breaches doubled this year. Your tools find thousands of CVEs. Most aren't exploitable. Backlogs grow while real risks wait.
Third-party code
False positive rates
Industry MTTR
Breaches via third-party
Reachability analysis has limits. Pixee goes deeper.
No more guessing. Every finding includes the specific conditions checked and why they don't apply to your codebase.
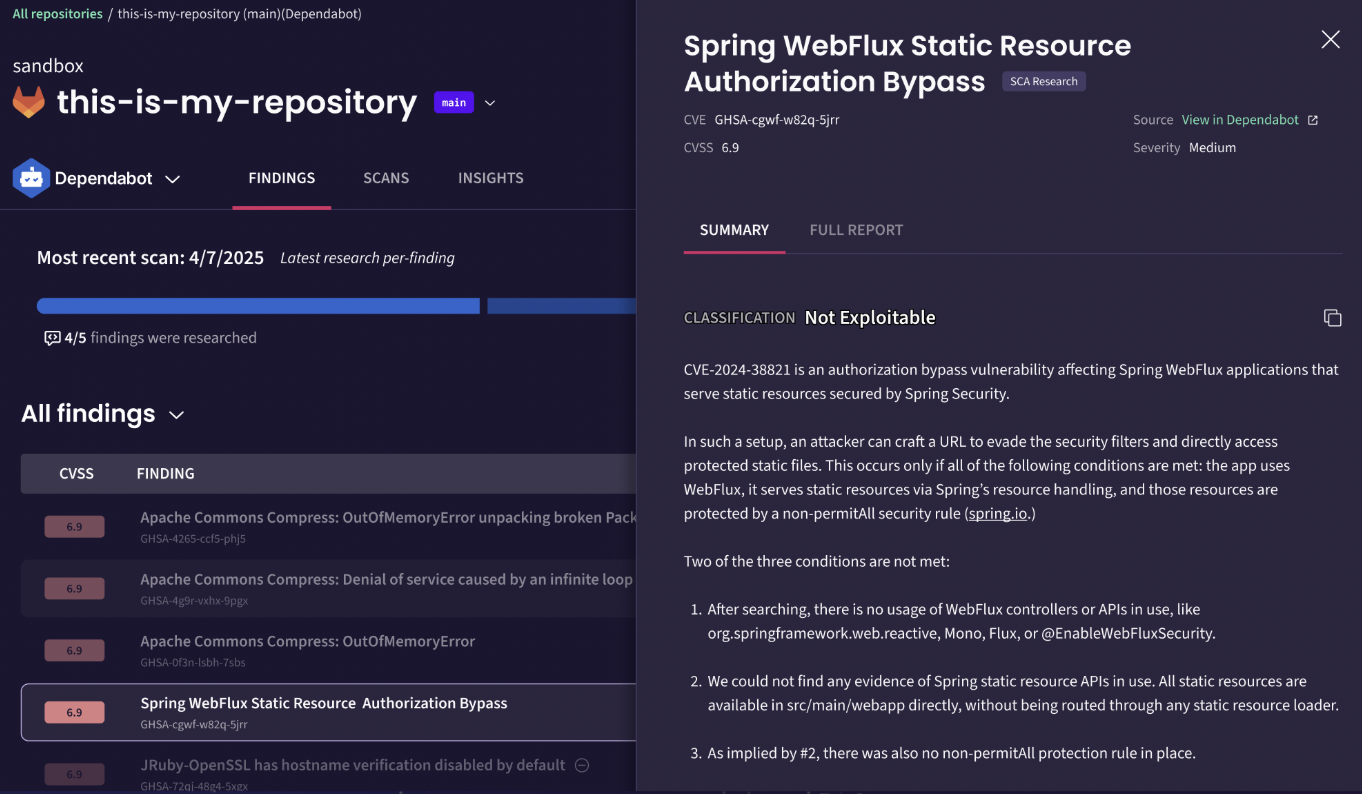
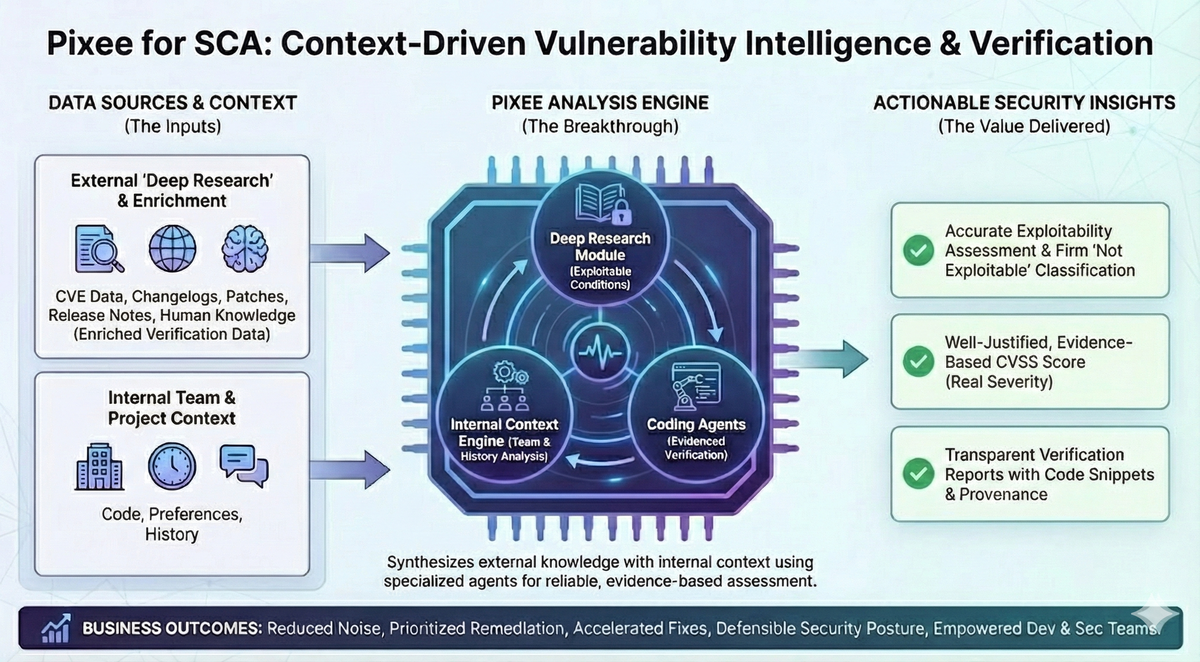
No more guessing. Every finding includes the specific conditions checked and why they don't apply to your codebase.
False positive elimination
Average review time per vulnerability
Time to value
Legacy SCA tools find vulnerabilities. They just can't tell you which ones matter. Pixee for SCA integrates with your current stack and immediately unlocks the ROI you've been looking for.