Q4 2025 Retrospective: 10 Stats That Defined the Quarter in AppSec

AI velocity met security capacity. Capacity lost.
Over the past three months, we've published 11 weeks of AppSec Weekly intelligence briefings. Each week brought fresh data on the collision between AI-accelerated development and security teams struggling to keep pace.
Looking back, Q4 2025 was the quarter where the gap became undeniable. Here are the 10 stats that tell the story.
1. AI-Generated Code Has 2.74x More Security Vulnerabilities
CodeRabbit's State of AI vs Human Code Generation Report analyzed 470 pull requests across open-source GitHub repositories: 320 AI-co-authored and 150 human-only.

The security gap was stark. AI-assisted PRs had 2.74x more XSS vulnerabilities, 1.91x more insecure object references, and 1.88x more improper password handling issues. The code quality gaps were even wider: 2.29x more incorrect concurrency control, 2.27x more null-pointer risks.
Why it matters: The productivity gains from AI coding tools come with measurable security costs. Teams adopting these tools need corresponding investment in automated security validation.
Read the full briefing: Dec 19-24
2. Nation-State Actors Automated 90% of a Cyberattack Using Claude AI
Anthropic disclosed that Chinese state-sponsored threat actors used Claude to automate reconnaissance, vulnerability identification, exploit crafting, and lateral movement. Not 10% automation. Not 50%. Ninety percent.

The same AI capabilities powering developer productivity now enable adversaries to execute attacks at equivalent speed.
Why it matters: Attackers have access to the same publicly available AI infrastructure as development teams. The arms race is symmetric.
Read the full briefing: Nov 15-19
3. 50% of CISOs Report Burnout Affecting Breach Preparedness
Nagomi Security's 2025 CISO Pressure Index painted a grim picture: 80% of CISOs report high or extreme pressure, 87% say it's increased over the last year, and 40% have considered leaving their roles.

The operational impact is measurable. 44% say burnout affects their ability to prepare for breaches. 65% oversee 20+ security tools, yet 58% say breaches occurred despite having tools in place to stop exactly that type of attack.
Why it matters: Security leadership is burning out faster than organizations can address root causes. Tool sprawl and AI attack surfaces compound the pressure.
Read the full briefing: Nov 8-12
4. 98% of Enterprises Deploy AI Agents, 79% Have No Written Security Policy
An EMA study revealed the governance gap: nearly every large enterprise (98%) is deploying AI agents, but 79% of organizations without written policies deployed anyway.
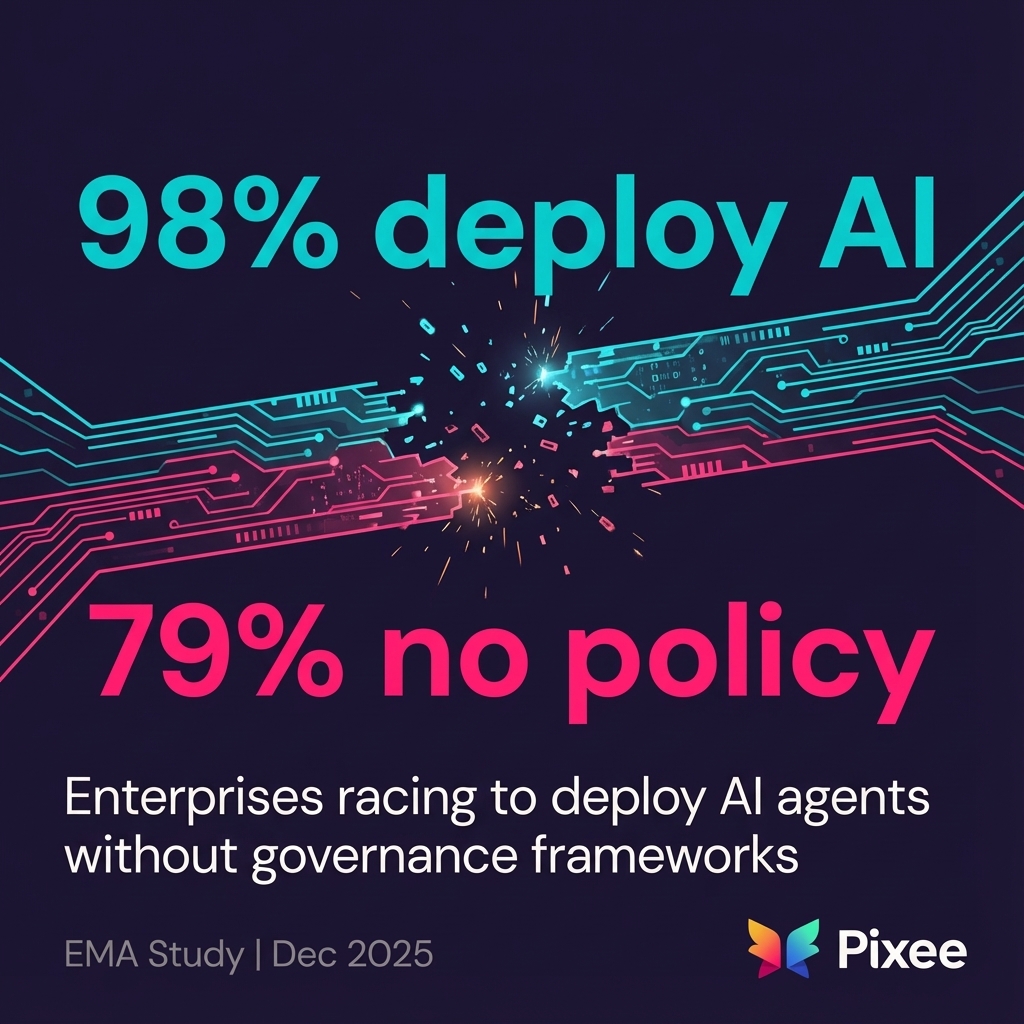
Current IAM infrastructure wasn't designed to authenticate software agents operating without human oversight. EMA warned of "agency abuse" attacks in 2026 where threat actors manipulate AI agents with excessive permissions.
Why it matters: The question isn't "do we have a policy" but "does our identity infrastructure actually support non-human autonomous actors."
Read the full briefing: Nov 27-Dec 3
5. React2Shell: 77,000+ Vulnerable Endpoints, Patch Broke Cloudflare
CVE-2025-55182 earned its CVSS 10.0 rating through textbook deserialization in React Server Components. Within hours of disclosure, nation-state actors weaponized it. Within 72 hours, 77,000+ vulnerable IP addresses were identified.

The emergency WAF rules Cloudflare pushed to mitigate the attack caused a global outage affecting Shopify, Zoom, and other major platforms. The fix literally broke production at scale.
Why it matters: React2Shell had everything it needed to get fixed: nation-state exploitation, CISA KEV entry, executive attention. Your backlog of medium-severity CVEs won't get the same treatment.
Read the full briefing: Dec 6-10
6. Shai-Hulud 2.0 Worm Compromised 25,000+ npm Packages in 7 Days
The Shai-Hulud 2.0 worm exploited npm's preinstall lifecycle hooks to propagate through the JavaScript ecosystem. It exfiltrated credentials from over 350 users and spread 10x faster than previous variants.

The attack surface is architectural. Preinstall hooks run with the same permissions as npm install itself. That design decision made sense when packages were human-reviewed; it becomes a liability when automated publishing enables mass infection.
Why it matters: Some organizations are now adopting --ignore-scripts as standard, accepting the breakage as the price of isolation.
Read the full briefing: Nov 20-26
7. 76% of Security Teams Can't Keep Pace with AI Code Velocity
CrowdStrike's survey quantified the capacity crisis: 76% of organizations are struggling to keep pace with the volume of code AI tools generate.

AI creates a bottleneck right where security teams live: the remediation pipeline. Code generation accelerates while code review, testing, and security validation remain human-paced.
Why it matters: You're facing a capacity crisis you can't hire your way out of. The constraint moved; the solution needs to move with it.
Read the full briefing: Oct 23-29
8. Attackers Exploited Oracle Zero-Days 2 Months Before Patches Existed
The Oracle E-Business Suite zero-day (CVE-2025-61882, CVSS 9.8) revealed a fundamental flaw in traditional vulnerability management. Threat actors discover and weaponize vulnerabilities faster than vendor disclosure cycles.

SLAs based on "patch within 30 days of release" don't account for exploitation starting 60 days before release. This isn't a patching speed problem. It's a fix architecture problem.
Why it matters: Compensating controls and runtime protection become first-line defense when attackers have months of lead time.
Read the full briefing: Oct 1-8
9. npm Package Hit 56,000 Downloads While Stealing Credentials
The lotusbail npm package accumulated 56,000+ downloads by delivering functional WhatsApp API capabilities. It also exfiltrated authentication credentials, session tokens, and message data.

This wasn't a typosquatting attack. Developers installed it because it worked. Traditional SCA tools scanning for known vulnerable dependencies would have cleared it. The malicious code wasn't a vulnerability; it was intentional functionality hidden alongside legitimate features.
Why it matters: Developer trust remains the most exploitable vulnerability. Attackers understand trust patterns well enough to weaponize them.
Read the full briefing: Dec 19-24
10. 3,000+ MCP Servers Breached in Largest AI Supply Chain Attack
A path traversal vulnerability in Smithery.ai compromised over 3,000 MCP servers and exposed thousands of API keys. MCP (Model Context Protocol) is the framework GitHub uses for AI agent tooling.

Teams adopting MCP workflows inherited new exposure in their dependency chains. Third-party dependencies became an active threat vector, not just a compliance concern.
Why it matters: AI development infrastructure is now a target. The attack surface extends beyond model security to the infrastructure running the agents.
Read the full briefing: Oct 23-29
The Through-Line: Velocity vs. Capacity
Q4 2025 was defined by a single tension: AI accelerates everything—code generation, attack execution, vulnerability creation—while security capacity remains structurally limited.
The organizations that adapted fastest shared a common pattern: they stopped trying to manually outrun the volume and invested in automation that could match the pace.
What We're Watching in 2026
• AI governance catching up: The 98%/79% gap will close as "agency abuse" attacks materialize
• Supply chain architecture changes: Expect npm and other registries to rethink preinstall hooks
• Automated remediation adoption: When 76% of teams can't keep pace, the market responds
• CISO role evolution: Burnout rates this high force structural changes
Stay Ahead Every Week
These insights came from 11 weeks of AppSec Weekly intelligence briefings. We publish every week, distilling the signal from hundreds of security news sources into actionable intelligence for practitioners.
No fluff. Just signal.

